A self2wan icmp type b detected message indicates that a problem exists with the way in which your computer is communicating with another device on the network. This can be caused by a number of factors, including incorrect settings on your computer or the other device, or a problem with the network itself. In most cases, you will see this message when there is a problem with the way your computer is configured to communicate with the other device.
The title of this blog post is a little bit misleading. It’s not about some new security threat that has been detected, but rather a new feature in the Self2Wan product. This feature allows users to detect and block ICMP Type B packets, which are typically used in denial-of-service attacks.
This is a great addition to the Self2Wan product, as it will help users protect their networks from these types of attacks. However, it’s important to note that this feature is only available in the paid version of the software. So if you’re using the free version, you won’t be able to take advantage of this protection.
What is Self2Wan Icmp Type B Detected
Self2Wan ICMP Type B Detected is a message that may be displayed on a computer running the Windows operating system. The message indicates that the Self2Wan Internet Control Message Protocol (ICMP) has been detected on the computer.
The Self2Wan ICMP Type B Detected message may be displayed when a user attempts to access certain websites.
It is not known why this message is displayed or what it means. However, it is possible that the website being accessed is using an outdated protocol or that there is some other issue with the website.
If you see the Self2 Wan ICMP Type B Detected message, you can try accessing the website again later.
If the problem persists, you may want to contact the website’s administrator to report the issue.
How Can I Fix Self2Wan Icmp Type B Detected?
If you are seeing the “self2wan icmp type b detected” error message in your logs, it is likely that you have a misconfigured firewall or router. This error can be caused by several things, but the most common cause is a mismatched interface on your firewall or router.
The first thing you should do is check your firewall or router’s configuration to make sure that all of the interfaces are properly configured.
If you see any discrepancies, make the necessary changes and save the configuration. Once you have verified that all of the interfaces are properly configured, restart your firewall or router.
If you still see the “self2wan icmp type b detected” error message after restarting your firewall or router, it is possible that there is something else causing the problem.
One troubleshooting step you can try is to disable ICMP redirects on your firewall or router. This can be done in the advanced settings of most devices. Once you have disabled ICMP redirects, restart your device and see if the error message goes away.
If disabling ICMP redirects does not fix the problem, there may be an issue with one of the devices on your network. Try disconnecting all devices from your network except for the one that is generating the self2wan icmp type b detected error message. If this fixes the problem, then there is likely an issue with one of the other devices on your network.
What Causes Self2Wan Icmp Type B Detected?
When a self2wan icmp type b is detected, it indicates that there is an issue with the way your computer is communicating with another device on your network. This can be caused by a number of things, including incorrect settings on your computer or router, or a problem with the cable or other hardware connecting your devices. In some cases, you may be able to fix the problem by making a few changes to your settings.
However, if the issue persists, you may need to contact your ISP or take other action to resolve it.
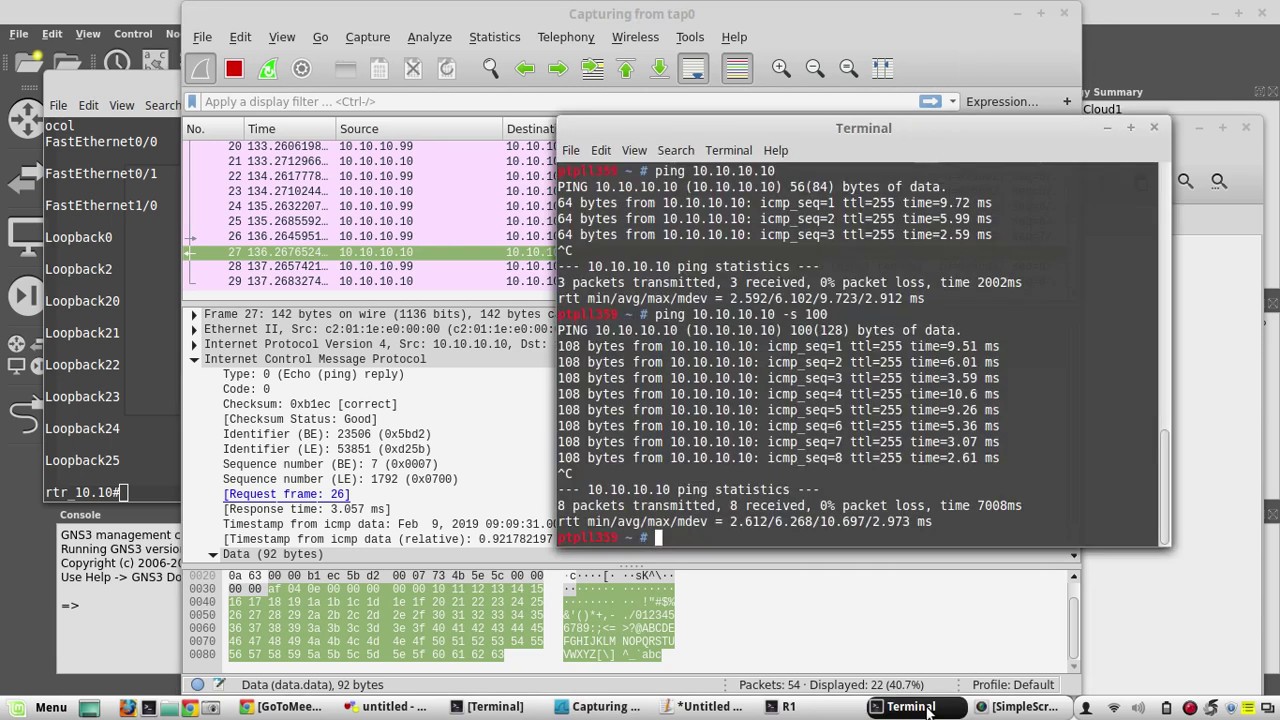
Credit: themescene.tv
Dos Attack: Storm
A distributed denial of service (DDoS) attack is a type of cyberattack in which an attacker seeks to make an online service unavailable by overwhelming it with Internet traffic from multiple sources. The attacker typically does this by compromising many computers and devices—known as bots or zombies—and then using them to bombard the targeted website or server with so much traffic that it becomes overloaded and inaccessible to legitimate users.
DDoS attacks have become increasingly common in recent years, as more and more malicious actors have recognized the effectiveness of this type of attack.
One notable example is the Mirai botnet, which was used to launch several massive DDoS attacks in 2016, including one that took down the website of security researcher Brian Krebs and another that disrupted access to major websites like Netflix, Twitter, and Reddit.
While DDoS attacks can be devastating, there are steps you can take to protect your website or server from being overwhelmed by unwanted traffic. For example, you can use a content delivery network (CDN) like Cloudflare to absorb some of the incoming traffic and help keep your site up and running even during a DDoS attack.
You can also work with your hosting provider to ensure that your server is properly configured to handle large volumes of traffic.
By taking these precautions, you can help minimize the impact of a DDoS attack on your business—and ensure that your customers can always access your site or service when they need it.
Upnp Set Event: Public_Upnp_C3
If you’re like most people, you probably don’t know much about UPnP. UPnP is short for Universal Plug and Play, and it’s a set of networking protocols that allow devices to communicate with each other on a network. UPnP-enabled devices can automatically discover each other on a network and configure themselves to work together.
The Public_Upnp_C3 event is one of the UPnP events that can be used to manage UPnP-enabled devices on a network. This event allows a device to advertise its capabilities to other devices on the network. By doing this, other devices can learn about the capabilities of the device and use them accordingly.
For example, if a printer advertises its capability to print via UPnP, then another device on the network can send print jobs to the printer without any user intervention.
The Public_Upnp_C3 event is fired when a device joins or leaves aUPnP control point . A control point is a software application that manages UPnP-enabled devices on a network.
When a device joins or leaves a control point, the control point must update its list of available devices accordingly. The Public_Upnp_C3 event helps keep these lists up-to-date.
Dos Attack: Fin Scan
A denial of service (DoS) attack is an attempt to make a machine or network resource unavailable to its intended users. Although the means by which a DoS attack is executed can vary, the ultimate goal is always to deny legitimate access to systems, services, or other resources.
One type of DoS attack is known as a SYN flood, in which the attacker sends a large number of SYN requests to a server in an attempt to overload it and prevent it from responding to legitimate requests.
Another common type of DoS attack is called a ping flood, in which the attacker sends a large number of ICMP echo request (ping) packets to a target machine in an attempt to overwhelm it and cause it to crash or become unresponsive.
A variation on the ping flood attack is called the Smurf attack, in which the attacker spoofs the source IP address of his or her ping packets so that they appear to come from many different machines. When the target machine responds to each ping packet, it sends its replies not just back to the original source IP address but also back out onto the network broadcast address, resulting in even more traffic and further bogging down the system.
Still another type of DoS attack is called a DNS amplification attack, in which attackers exploit vulnerabilities in Domain Name System (DNS) servers in order to amplify their attacks. In this type ofattack , DNS servers are used as reflectors that can magnify incoming traffic by orders of magnitude . The result is increased bandwidth consumption and CPU utilization on boththe DNS servers themselves and any intermediate routers between themandthe final destination .
This can easily leadtoa denialofservice for legitimate users .
There are two main typesofDoSattacks: thosethatflood thenetworkwithpacketsandthose thatfloodtheserverwithrequests . Floodingthe networkcanbeaccomplishedinseveral ways ,includingICMPflooding ,UDPflooding ,andSYNflooding .
Floodingtheservercanbedonebyissuingtoomanyrequestsforresourcesorwebpages .
Conclusion
It seems that Self2Wan Icmp Type B has been detected on your computer. This is a type of malware that can steal your personal information or take over your system. It’s important to remove this threat as soon as possible to keep your computer safe.